A solid security toolbox should form the heart of your defense, of course, but you'll also need to consider your basic behavior. For example, a leaked LinkedIn password does little harm if that particular alphanumeric combination only opens the door to that particular account, rather than every social media account you use. Two-factor authentication can stop a breach before it happens. And do your passwords suck?
I'm not trying to scare you. Rather, I'm interested in opening your eyes to the types of precautions that are necessary in the digital age—as evidenced by the biggest security exploits, blunders, and fails of 2012. 'Twas a banner year for the bad guys.
Honan hack attack

Over the course of a single hour, hackers gained access to Honan's Amazon account, deleted his Google account, and remotely wiped his trio of Apple devices, culminating in the hackers ultimately achieving their end goal: seizing control of Honan's Twitter handle. Why all the destruction? Because the @mat Twitter handle's three-letter status apparently makes it a highly coveted prize. (The malcontents posted several racist and homophobic tweets before the account was temporarily suspended.)
The devastation was all made possible by security snafus on Honan's end—daisy-chaining critical accounts, a lack of two-factor authentication activation, using the same basic naming scheme across several email accounts—and conflicting account security protocols at Amazon and Apple, which the hackers took advantage of with the help of some good ol' fashioned social engineering.
The scariest part? Most people probably employ the same basic (read: lax) security practices Honan did. Fortunately, PCWorld has already explained how to plug the biggest digital security holes.
The Flame virus
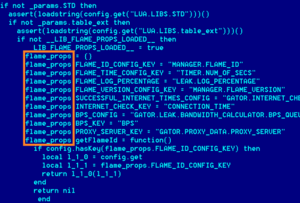
Once Flame sunk its hooks into a system, it installed modules that could, amongst other things, record Skype conversations or audio of anything happening near the computer, snag screenshots, snoop on network connections, and keep logs of all keypresses and any data entered into input boxes. It's nasty, in other words—and Flame uploaded all the information it collected to command and control servers. Shortly after Kaspersky researchers sussed out Flame's existence, the virus' creators activated a kill command to wipe the software from infected computers.
The $50 homebrew tool that unlocks hotel doors
At the Black Hat Security conference in July, researcher Cody Brocious unveiled a device could semi-reliably open electronic door locks made by Onity. Onity locks are found on 4 million doors in thousands of hotels across the world, including high-profile chains like Hyatt, Marriott, and IHG (which owns both Holiday Inn and Crowne Plaza). Based around an Arduino microcontroller and assembled for less than $50, the tool can be built by any crook with pocket change and some coding skills, and there's at least one report of a similar tool being used to break into hotel rooms in Texas. Arduino
ArduinoThe company eventually developed an actual solution for the vulnerability, but it involves swapping out the circuit boards of affected locks—and Onity refuses to foot the costs for doing so. A December ArsTechnica report suggests the company may be more willing to subsidize replacement boards in the wake of the Texas crime spree, though as of November 30th, Onity had only supplied a total of 1.4 million "solutions for locks"—including those plastic plugs—to hotels globally. In other words, the vulnerability is still very widespread. Epic fail.
Death by a thousand cuts
The year didn't see a massive database breach in the vein of 2011's PlayStation Network take-down, but a series of smaller penetrations came fast and furious throughout the spring and summer. While the release of 6.5 million hashed LinkedIn passwords may have been the most notable hack, it was buoyed by the posting of more than 1.5 million hashed eHarmony passwords, 450,000 Yahoo Voice login credentials, an unspecified number of Last.fm passwords, and the full login and profile information of hundreds of Nvidia forum users. I could keep going, but you get the point.What's the takeaway? You can't trust a website to keep your password safe, so you should use different passwords for different sites to minimize the potential damage if hackers do manage to puzzle out your login credentials for a given account. Check out our guide to building a better password if you need some pointers.
Dropbox drops its guard
 Dropbox
DropboxAt the same time, a very small number of users had their Dropbox accounts actively broken into by outside sources. Investigations revealed that the hackers gained access to the accounts because the victims were reusing the same username/password combination across several websites. When the login credentials were leaked in a breach at another service, the hackers had all they needed to unlock the Dropbox accounts.
Dropbox's woes highlight—again—the need to use separate passwords for different services, as well as the fact that you can't trust the cloud completely yet. You can take cloud security into your own hands with the help of a third-party encryption tool.
Millions of South Carolina SSNs pilfered
Speaking of encryption, it would be nice if the government followed basic security principals.After a massive October data breach resulted in a hacker obtaining the social security numbers of a whopping 3.6 million South Carolina citizens—in a state with just 4.6 million residents!— state officials tried placing the blame at the feet of the IRS . The IRS doesn't specifically require states to encrypt the SSNs in tax filings, you see. So South Carolina didn't—though it plans to start now, hindsight being 20/20 and all.
On the kinda positive side, debit and credit card details of 387,000 South Carolina citizens were also swiped in the digital heist and most of the those were encrypted, though that's likely little solace for the 16,000 people whose card details were stolen in plain-text form.
Skype's massive security flaw

Skype quickly plugged the hole when it caught the public eye, but the damage had already been done. The vulnerability was floating around on Russian forums and actively being used in the wild before it was shut down.
Hackers steal 1.5 million credit card numbers
In April, hackers managed to "export" a whopping 1.5 million credit card numbers from the database of Global Payments, a payment processing service used by government agencies, financial institutions, and around 1 million global storefronts, amongst others.Fortunately, the breach was fairly contained. Global Payments was able to identify the card numbers affected by the hack, and the data stolen only contained the actual card numbers and expiration dates, not any cardholder names or personally identifiable information. The hits kept coming, though. In June, Global Payments announced that hackers may have stolen the personal information of people who applied for a merchant account with the company.
Microsoft Security Essentials fails AV-Test certification
Well, isn't this embarrassing. AV-Test is an independent information security institute that regularly rounds up all the top antimalware products that are out there, tosses a whole bunch of nasties at said products, and sees how the various solutions hold up under the withering barrage. The organization did just that with 24 different consumer-focused security solutions at the end of November, and only one of those solutions failed to meet AV-Test's certification standard: Microsoft Security Essentials for Windows 7.
The blunder that wasn't: Norton source code released
It sounds scary on the surface: Groups of rogue hackers managed to get the source code for one of Symantec's popular Norton security utilities, then dumped the code on Pirate Bay for the world to dissect. Oh, noes! Now, nothing can stop the bad guys from running willy-nilly past the defenses that comes preinstalled on gajillions (approximately) of boxed systems sold throughout the world—right?Wrong. The source code belonged to Norton Utilities products released in 2006, you see, and Symantec's current products have since been rebuilt from the ground up, with no common code shared between the two. In other words, the 2006 source code's release doesn't pose any whatsoever risk to modern-day Norton subscribers—at least if you've updated your antivirus in the past half-decade.
Sign up here with your email

ConversionConversion EmoticonEmoticon